Getting Started with AWS Tuner
This guide walks you through onboarding AWS Tuner, from initial account setup to implementing your first cost optimizations.
Table of Contents
- Prerequisites
- Account Onboarding
- Initial Discovery & Analysis
- Understanding Recommendations
- Implementing Your First Optimizations
- Setting Up Scheduler
- Browser Extension Installation
- Best Practices
Prerequisites
Access Requirements
- CloudKeeper Account: Active CloudKeeper platform account
- AWS Account Access: AWS accounts to be optimized
- IAM Permissions: Ability to create IAM roles in target AWS accounts
- User Role: Minimum role of "Tuner User" in CloudKeeper platform
Technical Requirements
- Browser: Chrome, Firefox, Edge, or Safari (latest version)
- Network Access: HTTPS connectivity to CloudKeeper platform
- AWS Console Access: For implementing recommendations
Recommended Knowledge
- Basic AWS service familiarity (EC2, RDS, S3)
- Understanding of AWS pricing models (On-Demand, Reserved, Spot)
- AWS IAM role and policy concepts
Account Onboarding
Step 1: Access AWS Tuner
- Log in to CloudKeeper platform at
https://app.cloudkeeper.com - Click "Switch to Tuner" in the left navigation
- You'll be redirected to the Tuner dashboard
Step 2: Link Your AWS Account
Option A: CloudFormation StackSet (Recommended for Multiple Accounts)
# 1. Download CloudFormation template
wget https://cloudkeeper-public.s3.amazonaws.com/tuner/cloudkeeper-tuner-role.yaml
# 2. Create stack in AWS CloudFormation
aws cloudformation create-stack \
--stack-name CloudKeeperTunerRole \
--template-body file://cloudkeeper-tuner-role.yaml \
--parameters \
ParameterKey=ExternalId,ParameterValue=YOUR_EXTERNAL_ID \
ParameterKey=CloudKeeperAccountId,ParameterValue=123456789012 \
--capabilities CAPABILITY_NAMED_IAM
Option B: Manual IAM Role Creation
- Navigate to Tuner → Accounts → Link Account
- Click "Generate IAM Policy"
- Copy the generated IAM policy JSON
- In AWS Console → IAM → Roles → Create Role
- Select "Another AWS Account"
- Enter CloudKeeper Account ID:
123456789012 - Check "Require external ID" and enter your unique External ID
- Attach the generated policy
- Name role:
CloudKeeperTunerRole - Copy the Role ARN back to CloudKeeper Tuner
IAM Policy (Read-Only):
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2:Describe*",
"rds:Describe*",
"cloudwatch:GetMetricStatistics",
"cloudwatch:ListMetrics",
"pricing:GetProducts",
"ce:GetCostAndUsage",
"s3:ListBucket",
"s3:GetBucketLocation",
"dynamodb:DescribeTable",
"dynamodb:ListTables",
"redshift:Describe*",
"elasticache:Describe*",
"autoscaling:Describe*"
],
"Resource": "*"
}
]
}
Step 3: Verify Access
- Click "Verify Access" in Tuner
- Tuner will test IAM role assumption
- Wait for green checkmark: ✅ "Account linked successfully"
- Initial resource discovery begins automatically
Troubleshooting:
| Error | Cause | Solution |
|---|---|---|
| "AssumeRole failed" | External ID mismatch | Verify External ID matches exactly |
| "Access Denied" | Insufficient permissions | Review IAM policy, ensure all actions allowed |
| "Role not found" | Role ARN incorrect | Double-check Role ARN, ensure role exists |
Initial Discovery & Analysis
What Happens After Onboarding?
Timeline:
Hour 0: Account linked successfully
Hour 1: Resource metadata sync begins (EC2, RDS, S3, etc.)
Hour 4-6: CloudWatch metrics collection starts
Hour 24: First recommendations available
Hour 48: Full analysis complete (30-day lookback)
Monitoring Discovery Progress
Navigate to Tuner → Accounts → [Your Account] → Discovery Status:
✅ EC2 Instances: 456 resources discovered
✅ RDS Databases: 23 resources discovered
⏳ CloudWatch Metrics: Collecting (78% complete)
✅ EBS Volumes: 1,234 volumes discovered
✅ EBS Snapshots: 8,765 snapshots discovered
⏳ S3 Buckets: Analyzing (45% complete)
✅ NAT Gateways: 12 gateways discovered
✅ VPC Endpoints: 34 endpoints discovered
First Look at Your Environment
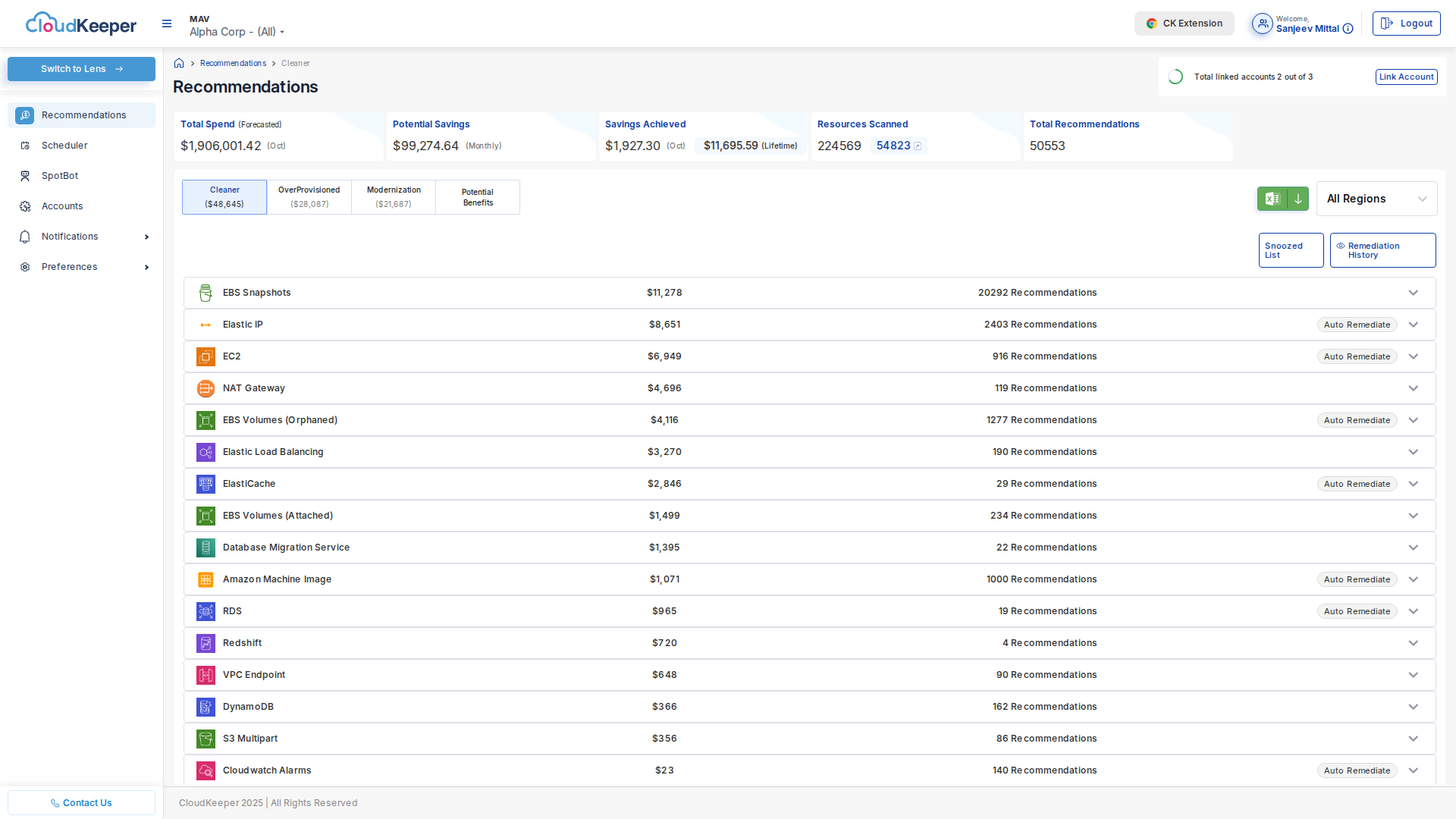
After 24 hours, check Tuner → Recommendations:
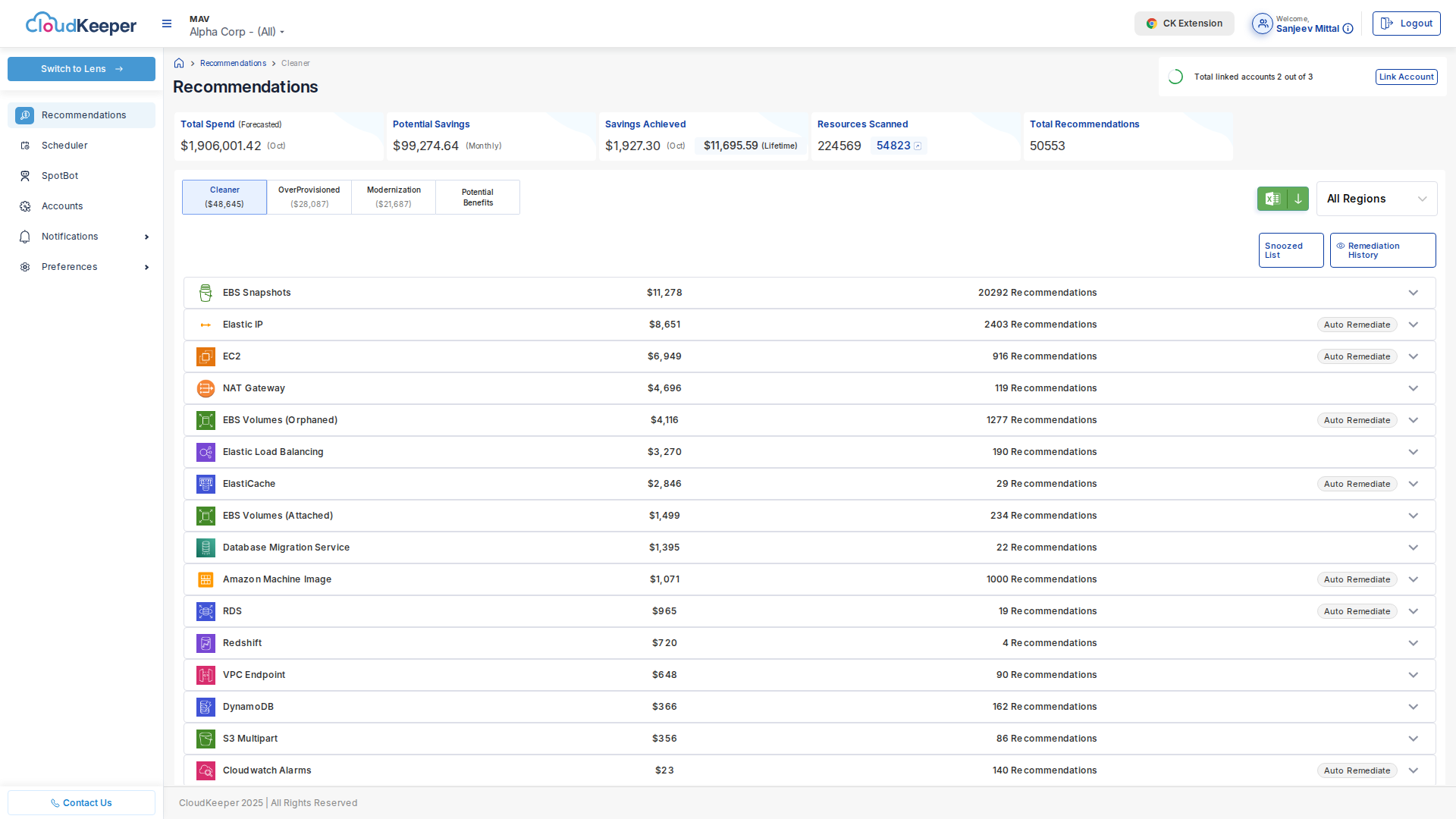
What You'll See:
Total Potential Savings: $XX,XXX/month
Category Breakdown:
├─ Cleaner: $XX,XXX/month (remove unused resources)
├─ OverProvisioned: $XX,XXX/month (rightsize over-allocated)
├─ Modernization: $XX,XXX/month (upgrade services)
└─ Potential Benefits: $XX,XXX/month (RIs & Savings Plans)
Understanding Recommendations
Recommendation Anatomy
Each recommendation contains:
- Category: Cleaner, OverProvisioned, Modernization, or Potential Benefits
- Resource Details: Instance ID, name, region, account
- Current State: Current configuration and cost
- Recommended Action: Specific change to implement
- Cost Impact: Monthly and annual savings
- Risk Level: Low, Medium, or High
- Metadata: Utilization metrics, sizing details
Example Recommendation:
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━
📋 EC2 Instance Rightsizing
Resource ID: i-0abcd1234efgh5678
Resource Name: api-server-prod-3
Region: us-east-1
Account: Production (123456789012)
Category: OverProvisioned
Risk Level: Medium
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━
Current Configuration:
Instance Type: m5.2xlarge
CPU: 8 vCPUs
Memory: 32 GB
Cost/Hour: $0.384
Cost/Month: $280.32
Utilization (30-day average):
CPU: 12% (max: 18%)
Memory: 25% (max: 32%)
Network: Low
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━
Recommended Configuration:
Instance Type: m5.large
CPU: 2 vCPUs
Memory: 8 GB
Cost/Hour: $0.096
Cost/Month: $70.08
Savings:
Monthly: $210.24 (75% reduction)
Annual: $2,522.88
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━
Action Required:
1. Test m5.large in staging environment
2. Monitor performance for 1 week
3. If acceptable, apply to production
4. Schedule change during maintenance window
Recommended By: Drools Rule Engine (oper_provisioned_ec2_instance_rules.drl)
Confidence: High (based on 30 days data)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━
Prioritizing Recommendations
Priority Matrix:
| Priority | Criteria | Typical Savings | Risk |
|---|---|---|---|
| P0 - Critical | > $5K/month, Low risk | $5K-$50K | Low |
| P1 - High | > $1K/month, Low-Medium risk | $1K-$5K | Low-Medium |
| P2 - Medium | > $100/month, Any risk | $100-$1K | Varies |
| P3 - Low | < $100/month | < $100 | Low |
Recommended Approach:
- Week 1: Implement all P0 cleaner recommendations (low-risk wins)
- Week 2-3: Test P1 rightsizing recommendations in non-prod
- Week 4: Implement P1 rightsizing in production with monitoring
- Month 2: Address P2 and modernization recommendations
Implementing Your First Optimizations
Quick Win: EBS Snapshot Cleanup
Goal: Remove orphaned EBS snapshots to save $5K-$15K/month
Navigate to Tuner → Recommendations → Cleaner:
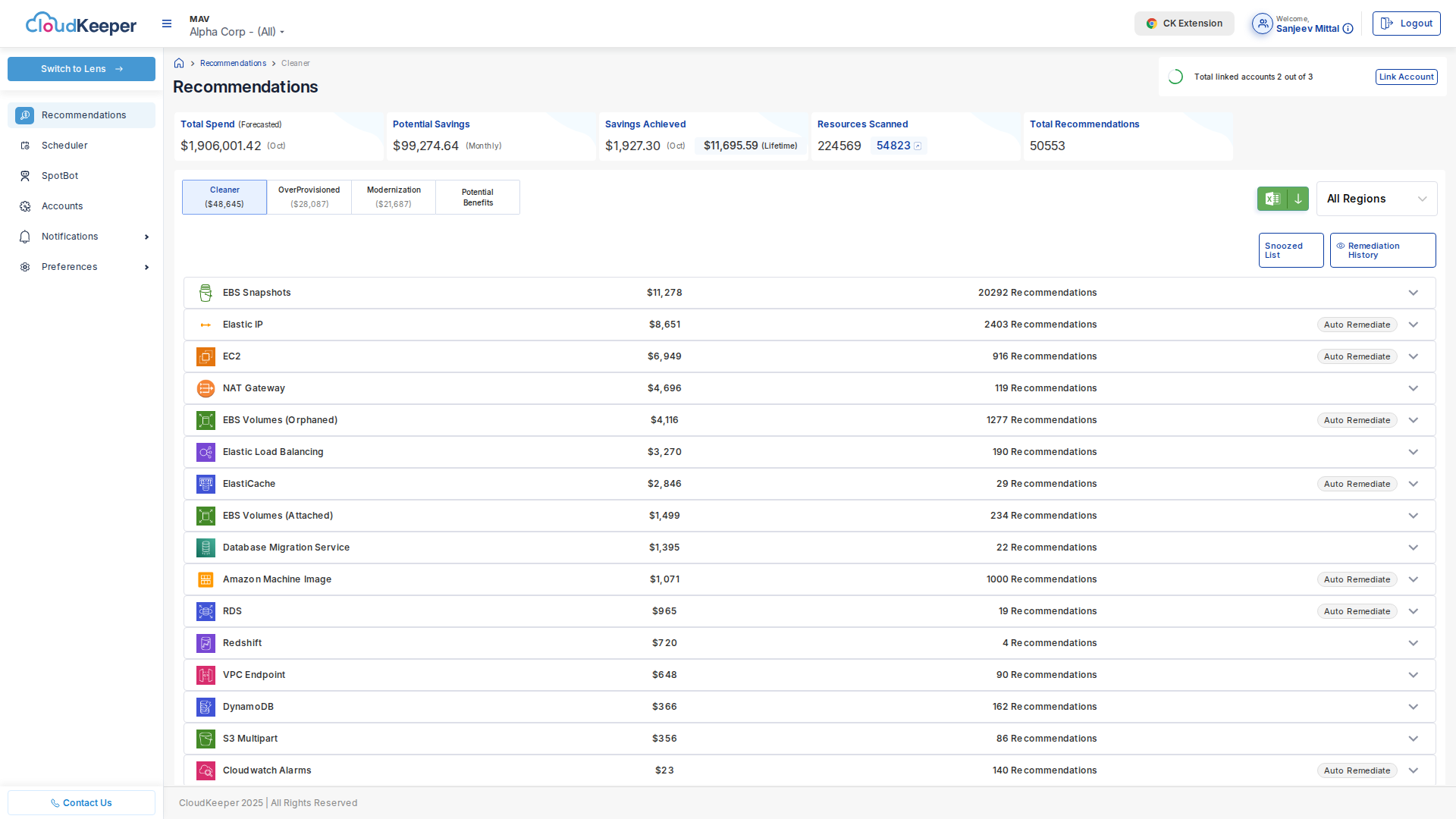
Step-by-Step:
-
Review Recommendations:
- Click "EBS Snapshots" tile
- Review list of snapshots recommended for deletion
- Filter by age: "Older than 90 days"
-
Validate Safety:
# For each snapshot, verify no attached volumes
aws ec2 describe-snapshots --snapshot-ids snap-0abcd1234 \
--query 'Snapshots[0].VolumeId'
# If Volume is deleted, snapshot is safe to remove -
Implement (Choose one):
Option A: Automated Remediation (Recommended)
- Check snapshots to delete
- Click "Auto Remediate"
- Confirm deletion
- Tuner deletes snapshots automatically
Option B: Manual Deletion
- Export snapshot IDs to CSV
- Use AWS CLI or Console to delete
- Mark as "Implemented" in Tuner
-
Monitor Results:
- Savings appear in next month's bill
- Tuner tracks realized savings vs. projected
Expected Results:
- Time to Implement: 30 minutes - 2 hours
- Monthly Savings: $5K-$15K (typical)
- Risk: Very Low (only deletes unattached snapshots)
Medium Impact: EC2 Rightsizing
Goal: Reduce EC2 costs by 20-40% through rightsizing
Navigate to Tuner → Recommendations → OverProvisioned:
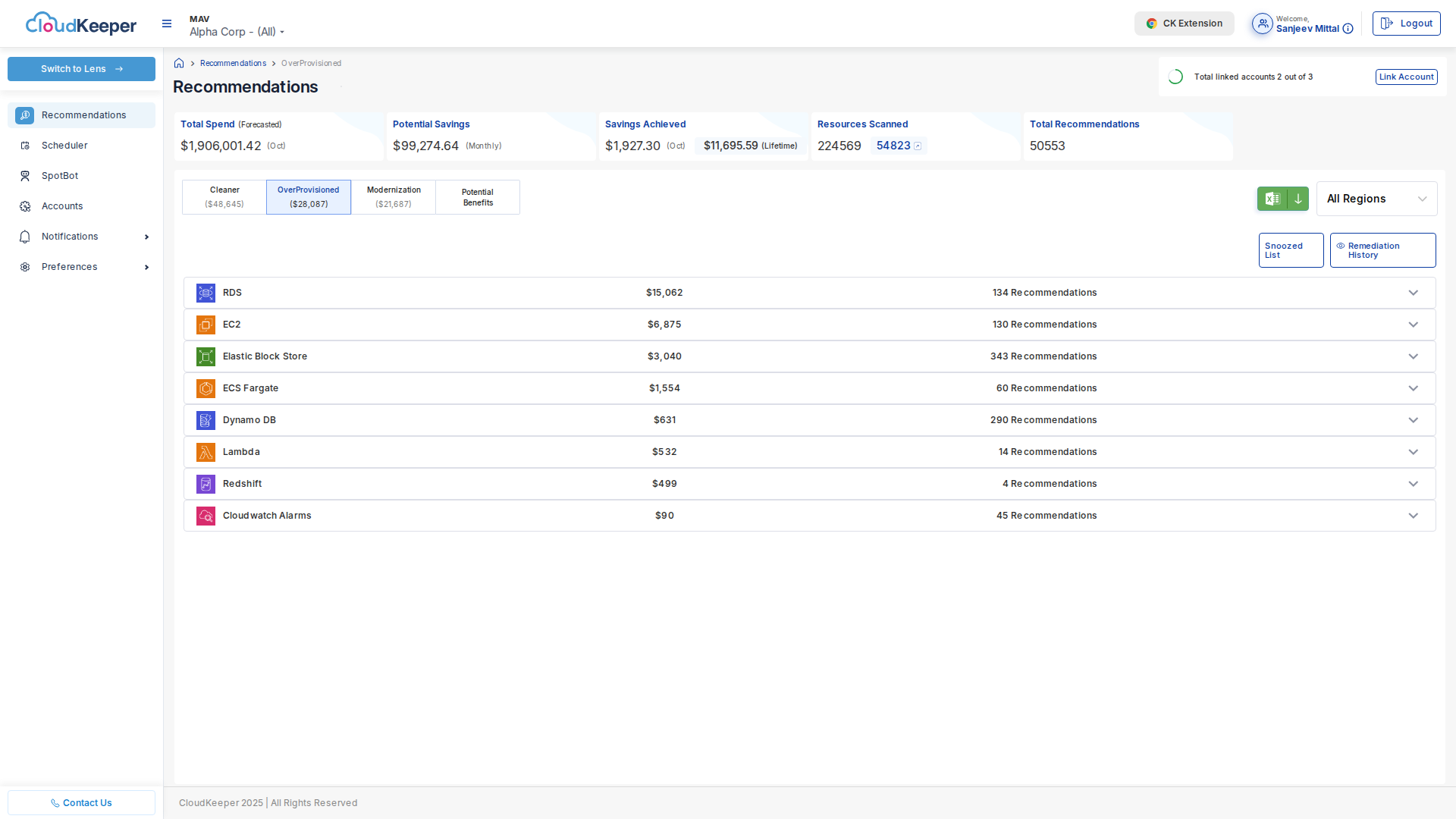
Step-by-Step:
-
Select Test Candidate:
- Start with non-production environment
- Choose instance with > $100/month savings
- Low utilization (< 20% CPU)
-
Validate Recommendation:
# Review CloudWatch metrics manually
aws cloudwatch get-metric-statistics \
--namespace AWS/EC2 \
--metric-name CPUUtilization \
--dimensions Name=InstanceId,Value=i-0abcd1234 \
--start-time 2025-09-26T00:00:00Z \
--end-time 2025-10-26T00:00:00Z \
--period 3600 \
--statistics Average,Maximum -
Test in Staging:
- Create AMI of current instance
- Launch new instance with recommended type
- Run load tests
- Monitor performance for 1 week
-
Implement in Production:
# 1. Stop instance
aws ec2 stop-instances --instance-ids i-0abcd1234
# 2. Modify instance type
aws ec2 modify-instance-attribute \
--instance-id i-0abcd1234 \
--instance-type m5.large
# 3. Start instance
aws ec2 start-instances --instance-ids i-0abcd1234
# 4. Monitor CloudWatch for 24 hours -
Mark as Implemented:
- In Tuner, click "Mark as Implemented"
- Tuner tracks actual savings vs. projected
Expected Results:
- Time to Implement: 1-2 weeks (including testing)
- Monthly Savings: $200-$500 per instance
- Risk: Medium (requires performance validation)
Setting Up Scheduler
Goal: Automatically stop non-production resources during off-hours
Navigate to Tuner → Scheduler:
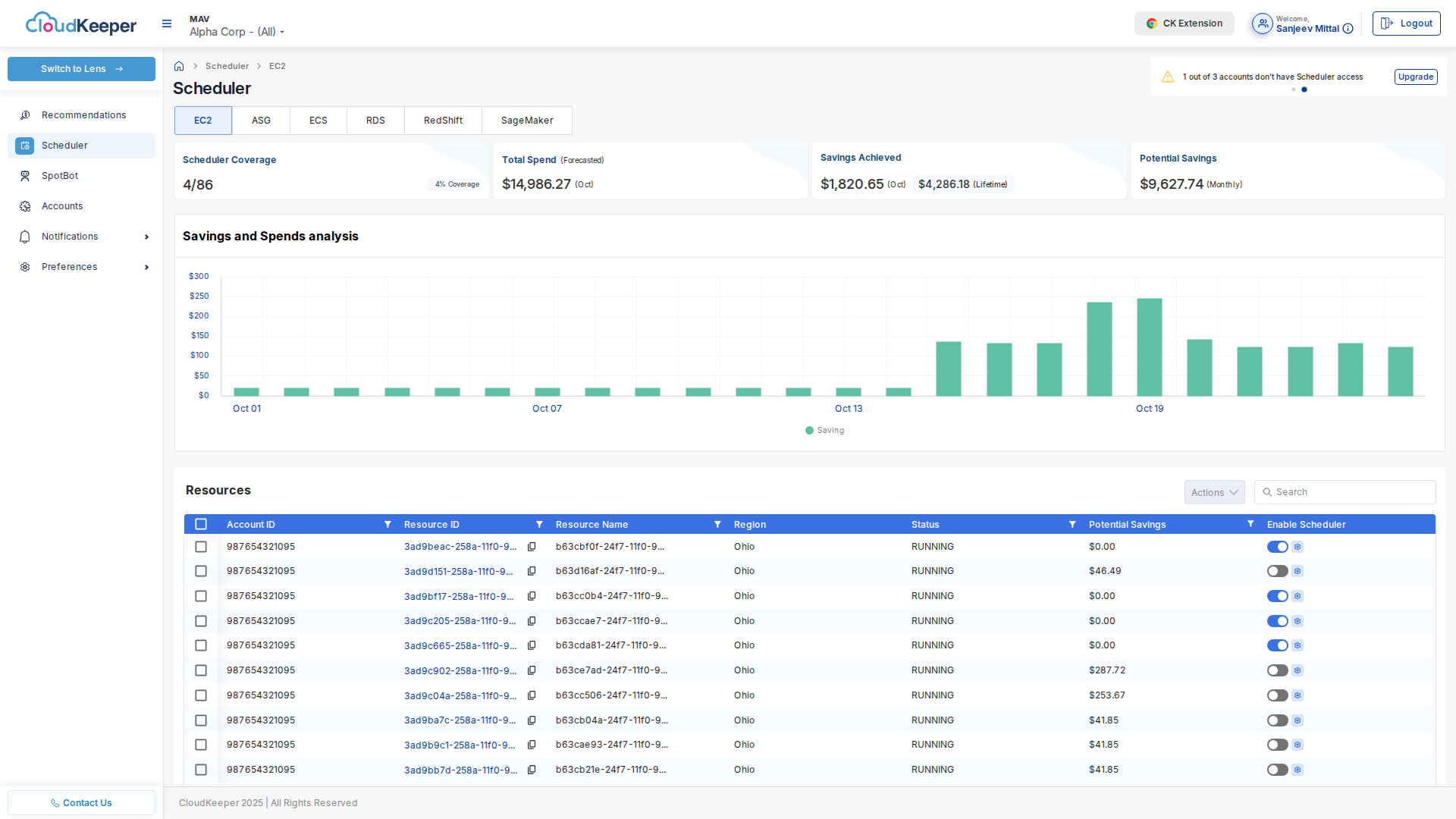
Basic Schedule Configuration
Use Case: Development environment used Monday-Friday, 8 AM - 7 PM
Step-by-Step:
-
Create Schedule:
- Click "Create Schedule"
- Name: "Dev Environment Schedule"
- Schedule Type: "Tag-Based"
-
Define Time Windows:
Start Time: Monday-Friday 7:00 AM EST
Stop Time: Monday-Friday 7:00 PM EST
Weekend: Completely off
Timezone: America/New_York -
Configure Tag Rules:
Match resources where:
- Tag Key: "Environment"
- Tag Value: "Dev"
AND
- Tag Key: "Scheduler"
- Tag Value: "Enabled" -
Select Resource Types:
- ✅ EC2 Instances
- ✅ RDS Databases
- ❌ Auto Scaling Groups (optional)
-
Safety Settings:
- ✅ Enable retry on failure
- ✅ Send email alerts
- ❌ Allow manual override (optional)
-
Review & Activate:
- Preview matched resources (e.g., 45 EC2, 12 RDS)
- Review projected savings
- Click "Activate Schedule"
Savings Calculation
Tuner automatically calculates expected savings:
Development Environment:
├─ 45 EC2 instances (avg $0.10/hr)
├─ Off hours: 127 hours/week
├─ Monthly off hours: 548 hours
└─ Monthly savings: 45 × $0.10 × 548 = $2,466/month
12 RDS databases (avg $0.15/hr):
└─ Monthly savings: 12 × $0.15 × 548 = $986/month
Total Monthly Savings: $3,452
Annual Savings: $41,424
Monitoring Scheduler
Dashboard Metrics:
- Success Rate: 99.2% (446/450 operations)
- Failed Stops: 2 (retry successful)
- Failed Starts: 2 (manual intervention required)
- Realized Savings: $3,387/month (98% of projected)
Browser Extension Installation
Goal: See Tuner recommendations directly in AWS Console
Installation Steps
-
Chrome Web Store:
- Visit Chrome Web Store
- Search: "CloudKeeper Tuner"
- Click "Add to Chrome"
-
Firefox Add-ons:
- Visit Firefox Add-ons
- Search: "CloudKeeper Tuner"
- Click "Add to Firefox"
-
Authentication:
- Log in to CloudKeeper web app
- Extension automatically captures JWT token
- Green badge indicates: ✅ Authenticated
Using the Extension
When viewing an AWS resource in AWS Console:
EC2 Instance Example:
┌─────────────────────────────────────────────────┐
│ 💡 CloudKeeper Tuner Recommendation │
├─────────────────────────────────────────────────┤
│ Instance: i-0abcd1234efgh5678 │
│ Current: m5.2xlarge ($280.32/month) │
│ CPU Utilization: 12% (30-day avg) │
│ │
│ Recommended: m5.large ($70.08/month) │
│ Monthly Savings: $210.24 │
│ │
│ [Implement] [Snooze 30 days] [Dismiss] │
└─────────────────────────────────────────────────┘
Actions:
- Implement: Creates Jira ticket or schedules change
- Snooze: Hide recommendation for 30/60/90 days
- Dismiss: Permanently dismiss (requires reason)
Best Practices
For Maximum Savings
-
Start with Low-Risk Wins:
- Cleaner recommendations first (snapshots, idle resources)
- Build confidence before rightsizing production
-
Use Phased Approach:
- Week 1: Non-production optimizations
- Week 2-3: Test production changes in staging
- Week 4+: Implement in production with monitoring
-
Enable Automated Remediation:
- Only for low-risk recommendations
- Review audit logs weekly
- Disable if unexpected issues arise
-
Schedule Non-Production Resources:
- Immediate 40-60% savings on dev/staging
- Zero performance impact on production
- Tag resources properly for accuracy
For Safety
-
Always Test First:
- Never apply rightsizing directly to production
- Use staging environment mirror
- Run load tests before production rollout
-
Monitor After Changes:
- CloudWatch alarms for CPU, memory, response time
- Application performance monitoring (APM)
- Rollback plan ready
-
Document Implementations:
- Track which recommendations implemented
- Note any issues encountered
- Share learnings with team
-
Review Monthly:
- New recommendations generated continuously
- Workload patterns change over time
- Adjust thresholds as needed
For Governance
-
Define Approval Workflows:
Low-Risk (< $500/month): Engineering team approval
Medium-Risk ($500-$5K): Engineering + Finance approval
High-Risk (> $5K): C-level approval required -
Tag Resources Properly:
- Environment: Dev/Staging/Prod
- Owner: Team responsible
- CostCenter: For chargeback
- Scheduler: Enable/Disable scheduling
-
Audit Trail:
- All changes logged in Tuner
- Export monthly reports
- Track realized vs. projected savings
Common Pitfalls to Avoid
❌ Don't:
- Implement all recommendations immediately without testing
- Ignore utilization spikes (e.g., month-end batch jobs)
- Disable scheduler without communication
- Delete snapshots without verifying no restore needs
✅ Do:
- Validate recommendations with your domain knowledge
- Consider workload patterns (daily, weekly, seasonal)
- Communicate schedule changes to developers
- Keep critical snapshots (disaster recovery)
Success Metrics
Track your optimization progress:
Month 1 (Discovery & Quick Wins):
- ✅ All accounts onboarded
- ✅ 100% snapshot cleanup completed
- ✅ Scheduler enabled for dev/staging
- 📊 Savings: 5-10% of AWS spend
Month 2 (Rightsizing Testing):
- ✅ Non-production instances rightsized
- ✅ Production test candidates identified
- 🧪 Performance testing in progress
- 📊 Savings: 10-15% of AWS spend
Month 3 (Production Rollout):
- ✅ Production rightsizing completed
- ✅ Modernization recommendations reviewed
- ✅ Spot instances for batch workloads
- 📊 Savings: 15-25% of AWS spend
Month 6 (Continuous Optimization):
- ✅ Reserved Instances purchased
- ✅ Automated remediation enabled
- ✅ Browser extension adopted by 80% of engineers
- 📊 Savings: 20-35% of AWS spend
Getting Help
Support Channels
- Email: support@cloudkeeper.com
- Slack: #tuner-support (if using CloudKeeper Slack Connect)
- Documentation: docs.cloudkeeper.com
- Status Page: status.cloudkeeper.com
Escalation Path
- Level 1: Tuner UI help documentation and tooltips
- Level 2: Email support (24-hour response SLA)
- Level 3: Customer Success Manager (existing customers)
- Level 4: Solutions Architect (enterprise customers)
Training Resources
- Video Tutorials: Available in Tuner → Help → Tutorials
- Live Demo: Schedule at calendly.com/cloudkeeper-demo
- Documentation: Complete guide at docs.cloudkeeper.com/tuner
Next Steps
- Review Key Features: Key Features & Capabilities
- Understand ROI: Business Value & ROI Examples
- Deep Dive on Architecture: Architecture Overview
Ready to get started? Link your first AWS account →